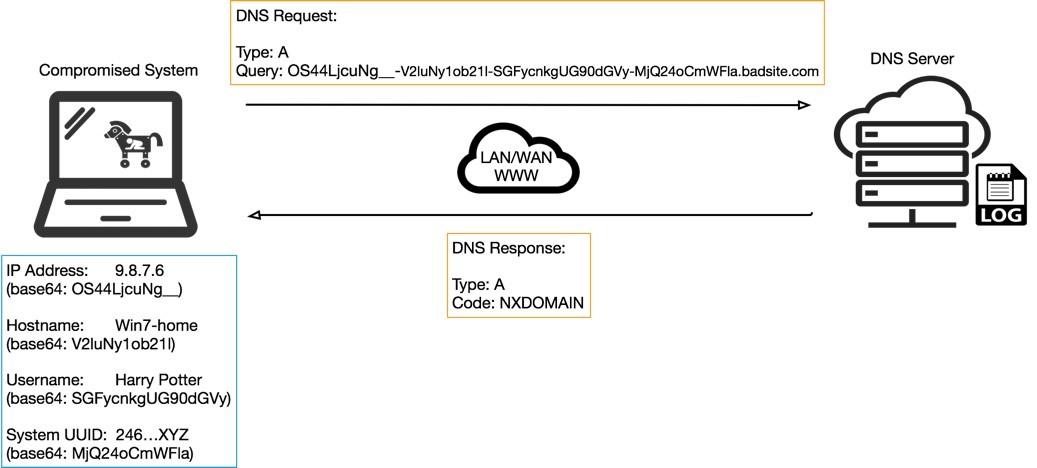
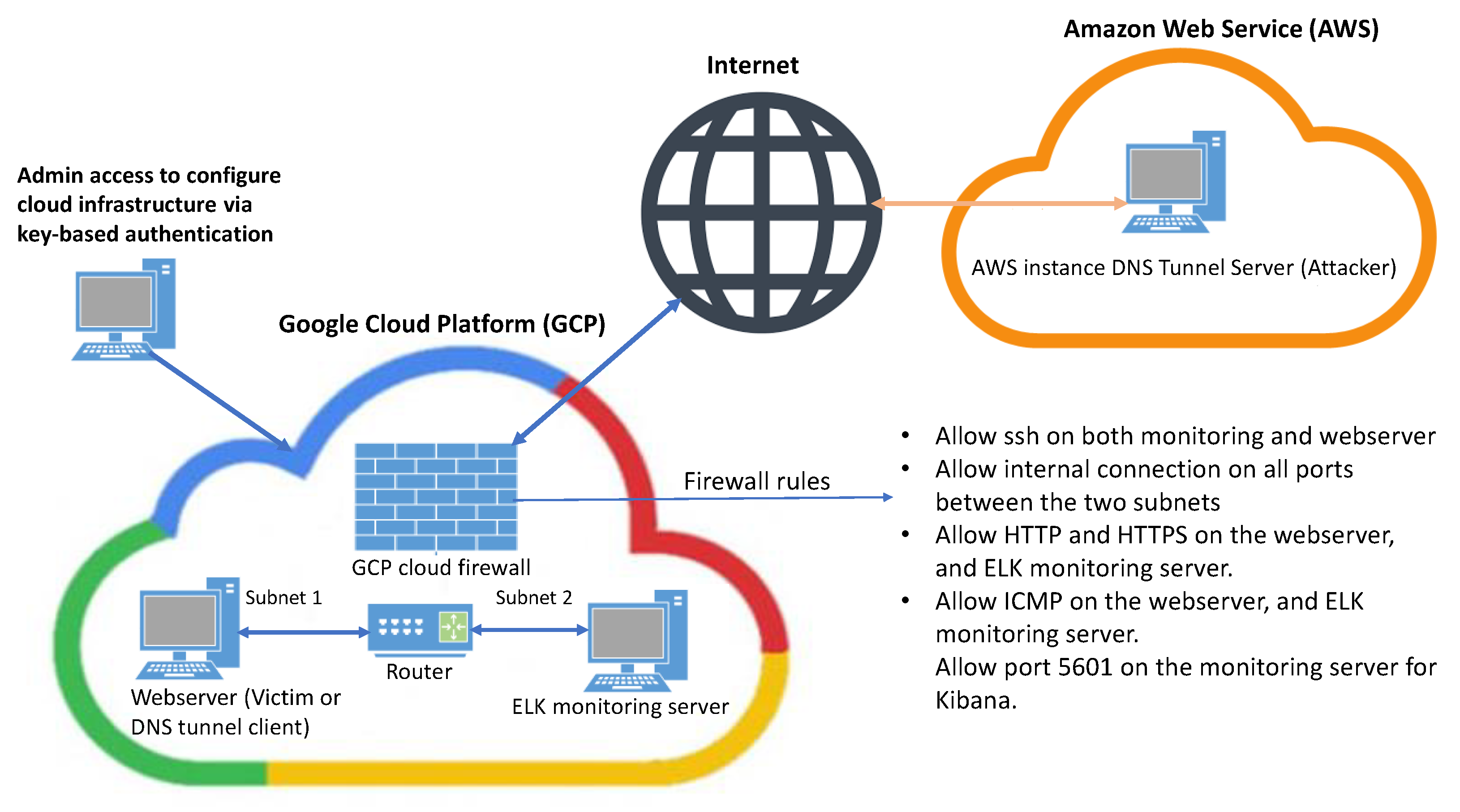
Identifying Malicious DNS Tunnel Tools from DoH Traffic Using Hierarchical Machine Learning Classification | SpringerLink

Do They Really Catch? | DNS Tunneling Vendor Test Series - Palo Alto NGFW | Ultra-slow & Heuristic - YouTube
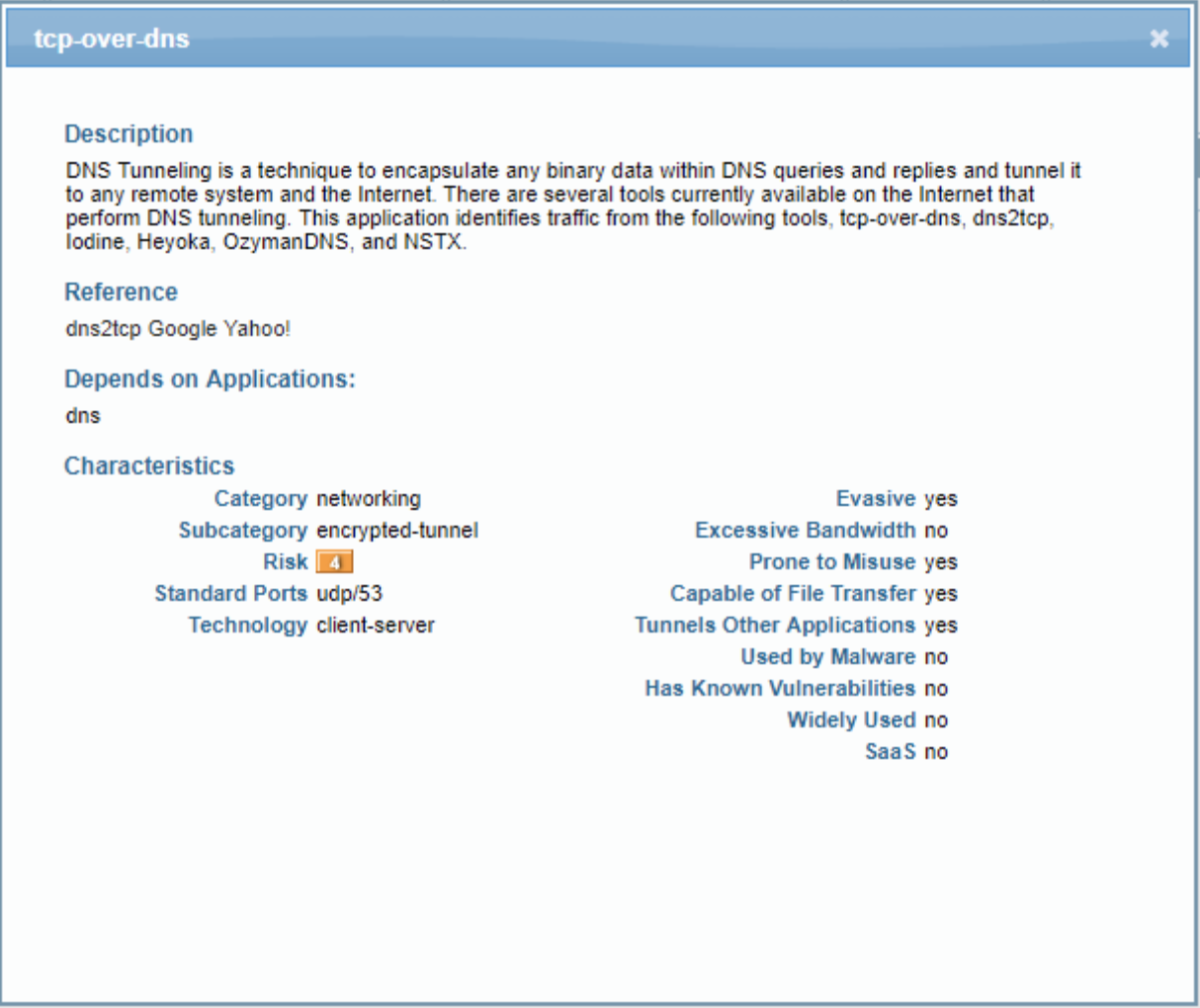
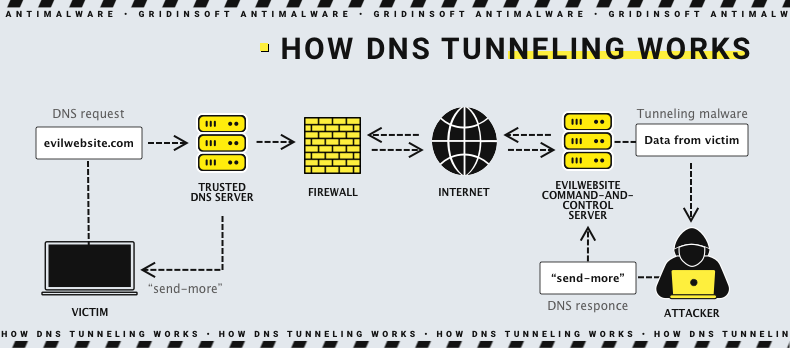
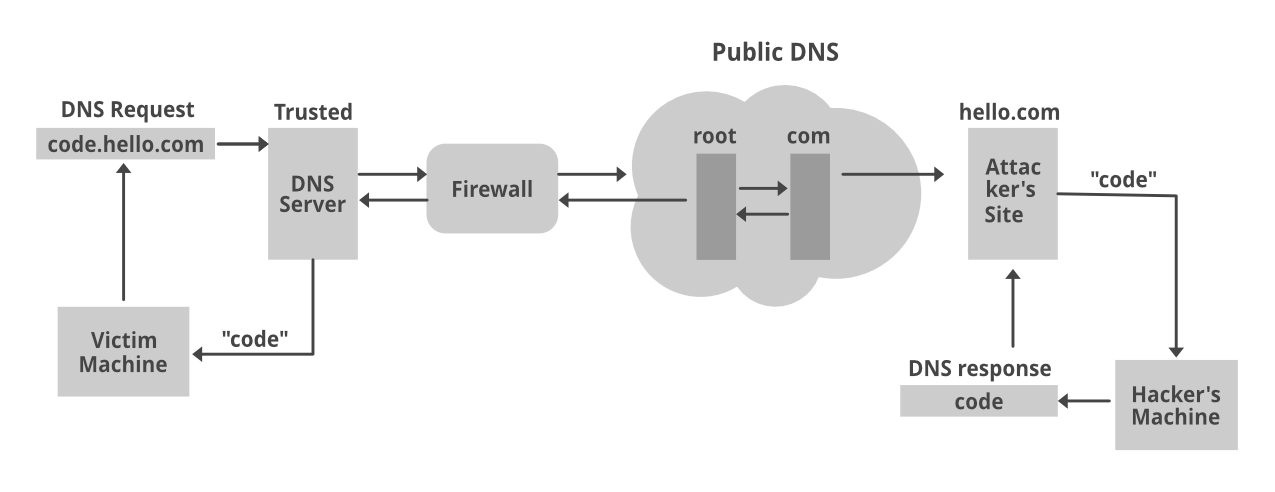
Learn how easy is to bypass firewalls using DNS tunneling (and also how to block it) | by Roger Galobardes | Medium